We at Brave Research just published a technical report called “Privacy and Security Issues in Web 3.0” on arXiv. This blog post summarizes our findings and puts them in perspective for Brave users.
DeFi resembles a financial Wild West: new sites pop up every other day, others implode, people make and lose a lot of money, without any safety nets or sound governance. What role does security and privacy play in all of this? Our paper set out to answer this question.
Findings
We began by compiling a list of 78 DeFi sites (including the top 50 sites by “total value locked”) and built a crawler to analyze those sites for security and privacy issues. You can see the full list below.
Despite the lightweight front ends, we find that several DeFi sites rely on third parties and occasionally even leak your Ethereum address to those third parties—mostly to API and analytics providers. Ethereum address leakage to Google is particularly problematic because the company likely already has PII about you, which it can then link to your Ethereum address, which can then be linked to your transaction history on the blockchain. Google, being an advertising business, has an incentive to monetize that data.
We also find that many sites embed third party scripts—which is always a security risk but that risk is particularly pronounced in DeFi given that funds are at stake, and third party scripts could phish the user by initiating fraudulent wallet transactions, and by manipulating the DeFi site’s DOM, to make it more likely that the user accepts the fraudulent transaction. Among our 78 DeFi sites, 48 (66%) embed at least one third party script from a total of 34 third parties. Unsurprisingly, Google’s presence among those scripts is pervasive: 41 DeFi sites (56%) embed at least one script provided by Google.
The table at the bottom of this blog post contains the raw numbers.
What does this mean for Brave users?
Brave users are generally not affected by Google’s presence among DeFi sites because Brave blocks Google Analytics by default. This means that Google doesn’t get to see what DeFi sites you visit, and doesn’t get to learn your Ethereum address—at least not in this way. The same is true for other trackers, like the ones from Hotjar or Facebook, which we found on some DeFi sites.
Countermeasures
Brave blocking tracking scripts goes a long way towards using DeFi in a private setting but it is no panacea. For example, your Ethereum address may still leak to third parties. Is there a way to use DeFi while being in full control of your Ethereum address?
As part of this project, we built a proof-of-concept patch for MetaMask (we focused on MetaMask because of its popularity) that does just that: after clicking on the “connect wallet” button, the patch replaces the user’s “real” Ethereum address with a deterministic, site-specific address that is derived from your real address (for details, take a look at Section 5 in our paper).
Your real Ethereum address may be 0x123…def but our patch makes it so that Uniswap sees 0x321…789 and Compound may see 0xabc…987. This makes it harder (but not impossible!) for DeFi sites and third parties to learn your real Ethereum address, or link your browsing activity across DeFi sites.
To make the above work, we had to engage in some trickery. For example, if we hand out fake addresses to a DeFi site, the site will display incorrect balances, and transactions won’t be valid. We work around that in our patch by transparently replacing wallet balances and Ethereum addresses so that DeFi sites can be meaningfully used. The diagram below illustrates the idea: a user visits example.finance, and their MetaMask extension hands the site a derived Ethereum address, but makes sure that the balance is correct. Our patch rewrites transactions so that they contain the user’s real Ethereum address before making it onto the blockchain.
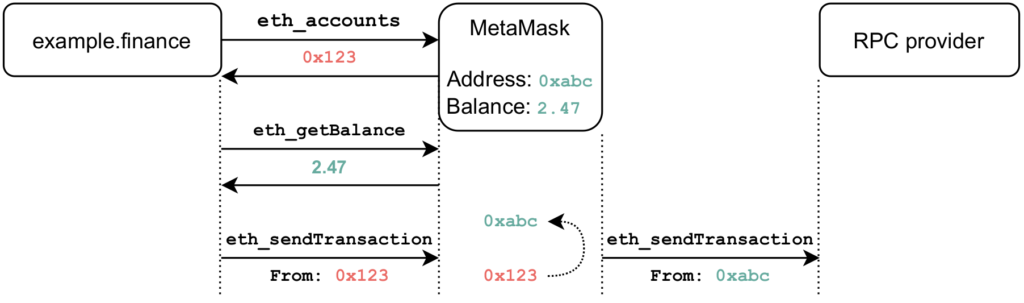
Note that at this point, our patch is a proof-of-concept and not ready for production. Regardless, it demonstrates that there is room for privacy improvements in DeFi, and we will continue raising the bar in our upcoming Brave Wallet.
Conclusion
Ethereum addresses constitute sensitive, private information, akin to credit cards and bank account numbers. DeFi sites should treat them accordingly, and never reveal Ethereum addresses to third parties unless they have a very good reason. The “De” in DeFi stands for “decentralized” and it’s important that DeFi lives up to that by refraining from using centralized API or analytics providers.
Our work also highlights how well-established Web development practices like the embedding of third party scripts is particularly problematic in the context of DeFi, and results in Google being able to track DeFi users across sites, and potentially link their Ethereum address to the PII that Google likely already has.
Appendix
The following table shows the subset of 53 DeFi sites that embed at least one third party script (second column) or leak the user’s Ethereum address to at least one third party (third column). We collected the data on August 27, 2021. Note that those numbers are a lower bound because we might have missed some address leaks.
| Origin | No. of Scripts | No. of Leaks |
|---|---|---|
| zerion.io | 9 | 3 |
| 1inch.io | 8 | 1 |
| dydx.exchange | 6 | 0 |
| o3swap.com | 5 | 0 |
| opensea.io | 4 | 0 |
| instadapp.io | 4 | 0 |
| bancor.network | 4 | 2 |
| airswap.io | 4 | 0 |
| rarible.com | 3 | 1 |
| balancer.fi | 3 | 0 |
| swapswap.org | 2 | 0 |
| sushi.com | 2 | 0 |
| saddle.exchange | 2 | 0 |
| opyn.co | 2 | 0 |
| notional.finance | 2 | 0 |
| jelly.market | 2 | 1 |
| idle.finance | 2 | 0 |
| foundation.app | 2 | 0 |
| dodoex.io | 2 | 2 |
| bifi.finance | 2 | 3 |
| alphafinance.io | 2 | 0 |
| aave.com | 2 | 0 |
| zapper.fi | 1 | 0 |
| yield.is | 1 | 0 |
| yearn.finance | 1 | 4 |
| wing.finance | 1 | 0 |
| wasabix.finance | 1 | 0 |
| warp.finance | 1 | 0 |
| vesper.finance | 1 | 0 |
| uniswap.org | 1 | 0 |
| truefi.io | 1 | 0 |
| synthetix.io | 1 | 0 |
| sablier.finance | 1 | 1 |
| ribbon.finance | 1 | 0 |
| reflexer.finance | 1 | 1 |
| rari.capital | 1 | 0 |
| rampdefi.com | 1 | 0 |
| pickle.finance | 1 | 0 |
| pancakeswap.finance | 1 | 0 |
| oasis.app | 1 | 0 |
| moonswap.fi | 1 | 0 |
| maple.finance | 1 | 0 |
| inverse.finance | 1 | 0 |
| indexcoop.com | 1 | 0 |
| impermax.finance | 1 | 1 |
| for.tube | 1 | 0 |
| dmm.exchange | 1 | 0 |
| dfyn.network | 1 | 0 |
| debank.com | 1 | 0 |
| codefi.network | 1 | 0 |
| boringdao.com | 1 | 0 |
| loopring.io | 0 | 2 |
| defisaver.com | 0 | 3 |









