Brave and UC San Diego announce SugarCoat, a new solution to strengthen the protection of Web users’ privacy while not breaking websites
This is the twelfth post in an ongoing, regular series describing new privacy features in Brave. This post presents the results of a research collaboration between Brave Software and the University of California at San Diego. The work was done by Michael Smith and Deian Stefan at UC San Diego, and Peter Snyder, Shivan Sahib, and Ben Livshits at Brave Software.
The TL;DR;
The research was presented at the 2021 ACM Conference on Computer and Communications Security (CCS) by UC San Diego Doctorate Student Michael Smith on November 15th. A preprint of the paper is available today.
Problem: Privacy Protections can Break Websites
SugarCoat is the solution to a common problem in Web privacy: how to protect Web users from Web sites that expect to be able to violate user privacy. Popular privacy tools like content blockers (sometimes called ad-blockers) often face a lose-lose choice when users visit a privacy-harming website. Either block the privacy-harming page functionality and break the website, or prioritize making sure the page works correctly but exposing the browser user to the privacy harm they wished to avoid in the first place.
Privacy tools like the terrific uBlock Origin project have attempted to solve this problem by creating alternate, privacy-protecting versions of tracking libraries, scripts that maintain the benign parts of tracking code while removing the privacy harming parts. This approach has proven very effective, and Brave has incorporated and contributed to such projects.
However, though useful, this approach has a serious limitation; generating privacy-preserving versions of tracking libraries is a difficult and tedious task. Tracking libraries are large, complex and sometimes intentionally-obfuscated. As a result, the privacy community is limited in the number of privacy-preserving alternative-versions of tracking scripts it can maintain.
SugarCoat: Privacy or Compatibility, Pick Any Two
SugarCoat helps solve this privacy-v.s.-compatibility trade-off by automating the creation of privacy-preserving implementations of tracking libraries. Brave will both deploy SugarCoat generated scripts this year in the Brave browser, and publish them so they can be used by other popular content blocking tools (including the previously mentioned uBlock Origin project).
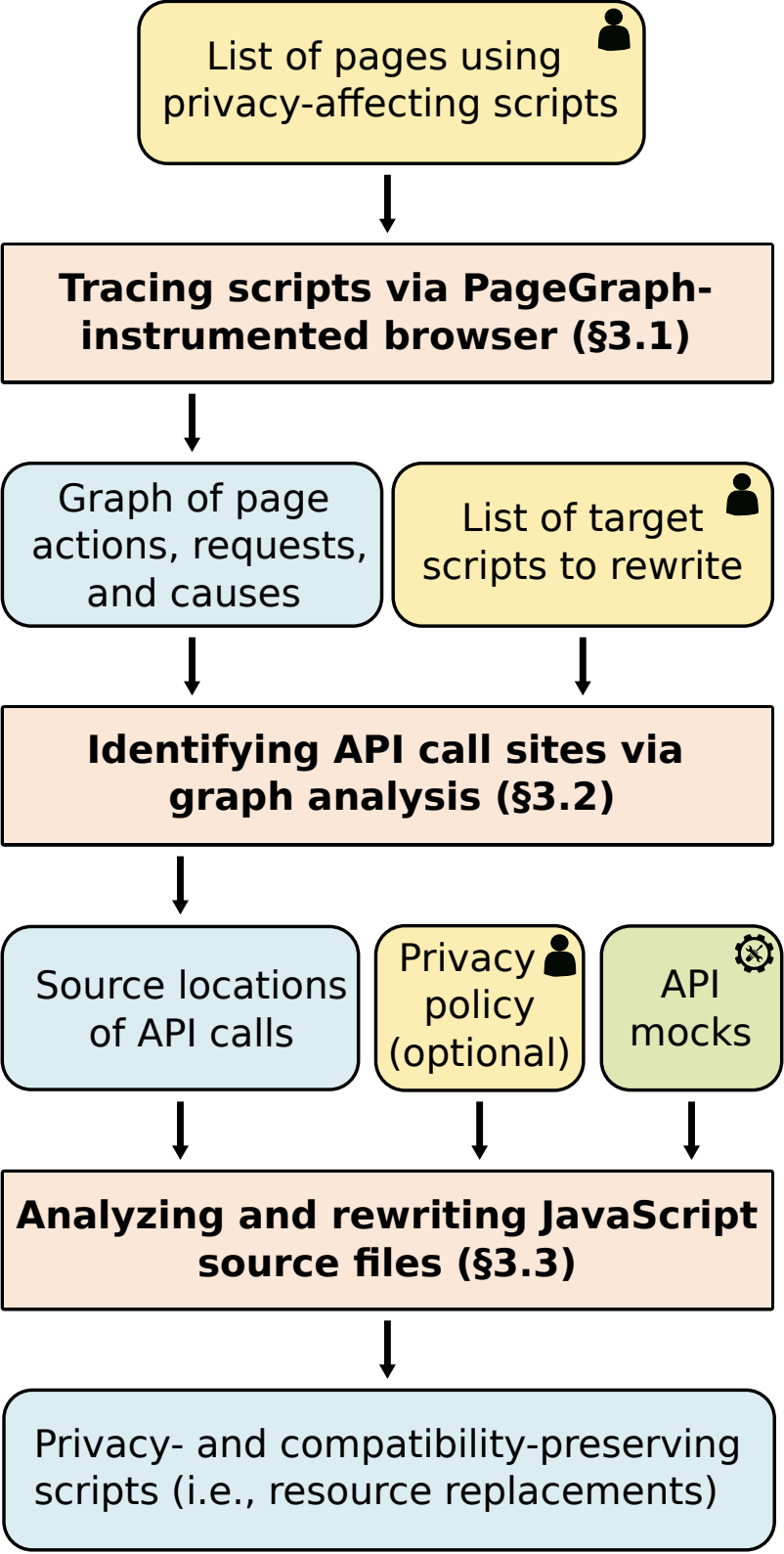
At a high level, SugarCoat works in two steps: first, by using Brave’s PageGraph system to analyze how a page uses a tracking library, including which Web APIs the script uses and what additional scripts the tracking library pulls in. SugarCoat then uses this information to rewrite the tracking library, by replacing calls to privacy-affecting Web APIs with alternative, “mock” implementations of the same APIs. These mock API implementations look the same to the tracking library, but prevent the underlying privacy harm from occurring. SugarCoat incorporates a range of techniques to ensure that the benign parts of tracking libraries continue to work as expected, and that only privacy-relevant behaviors are modified.
The SugarCoat process can be run in a fully automated manner, allowing SugarCoat to be deployed at Web scale, against tens of thousands of sites if needed. Being able to run fully automated is critical, so that SugarCoat can keep up to date with scripts that try to evade SugarCoat or sites that frequently change.
The full details of the SugarCoat pipeline can be found in the research paper.
Deploying SugarCoat in Brave Browsers
Brave will begin rolling out SugarCoat generated scripts to Brave browser users in Q4 2021. Brave is also excited to work with the maintainers of popular content blocking tools so they can also enhance the privacy of their users’ browsing. The source code for SugarCoat, and the automation framework around it, are fully open source. Brave will also share, grow and keep up-to-date the privacy-preserving alternative libraries generated by SugarCoat, so that they can be incorporated by other privacy tools.






