Debouncing
This is the eleventh post in an ongoing, regular series describing new privacy features in Brave. This post describes work done by Senior Software Engineer Mark Pilgrim and Filter List Engineer Ryan Brown (@fanboynz), and was written by Director of Privacy Peter Snyder.
The TL;DR;
Brave is releasing additional protections against certain forms of bounce tracking. We call these new protections “debouncing”. As of desktop version 1.32, Brave will protect users against bounce tracking by recognizing when the user is about to visit a known tracking domain, skipping visiting the tracking site all together, and instead directly navigating the user to the intended destination. Debouncing is available in nightly versions of Brave now, and will be rolled out to all Brave users shortly.
Bounce Tracking (or, Jerks Refuse to Take “No” for an Answer)
Bounce tracking is another technique trackers use to try and violate your privacy and follow you around the Web. Bounce tracking is an attempt to circumvent restrictions on third-party storage in privacy-focused browsers. The technique works by injecting additional sites between a site you’re visiting, and the site to which you intend to navigate. These intermediate sites over time learn what sites you’ve visited, and so can perform the same kinds of tracking sites used to use third-party cookies for.
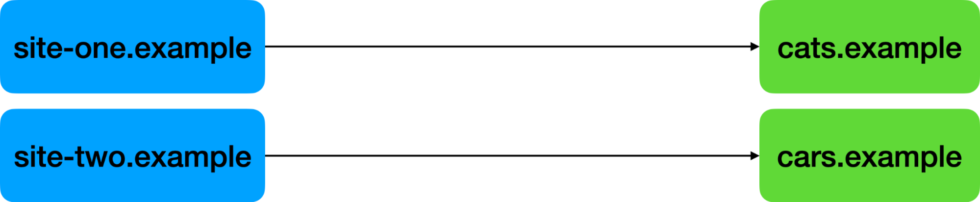
As a simplified example of how bounce tracking works, consider the following example. A browser user is visiting the site site-one.example, and clicks on a link to go to cats.example. Later, the same user visits a different site, site-two.example, and clicks on a link to go to cars.example. This could look like the below.
Bounce trackers change the above, desirable situation by inserting a new, unwanted, tracking site in each navigation. When a user clicks on a link to cats.example, they’re instead taken to an unrelated site, at an URL like https://tracker.example/record?dest=cats.example. The tracking site then records that the user is interested in cats.example, and then quickly redirects the user to cats.example. The same process might then repeat when the user tries to visit cars.example; the user is instead directed to tracker.example, which learns that the same person that was interested in cats is also interested in cars, before redirecting the user to the intended page on cars.example. This might look like the below.

“Debouncing” to Defeat Bounce Tracking
Brave’s new debouncing feature protects users against bounce tracking by observing when (using the above example) the browser is about to visit tracker.example, recognizing that the “dest” parameter includes the intended destination URL, and replacing the navigation to tracker.example with the intended final URL. Brave’s “debouncing” feature not only protects users against bounce tracking among websites, but also bounce-tracking URLs used in other places on the web, including links in affiliate marketing emails.
Brave uses a Brave maintained list to identify bounce tracking URLs. This list is maintained by Brave, and is drawn from a mix of crowd-sourcing and existing open-source projects, including the terrific URL Tracking Stripper extension, Link Clearer extension, and Clear URLs extension, along with additional rules maintained by Brave. Brave will maintain this combined list going forward and welcomes collaboration with other similar projects.
One More Defense Against Bounce Tracking
Debouncing is yet another way Brave protects users against bounce tracking. Debouncing exists alongside other bounce tracking protections in Brave: query parameter stripping and warning users when they’re about to visit a suspected bounce tracking site. Brave is planning additional protections against bounce tracking as well, which we are excited to announce shortly. Brave is also working in the W3C to help standardize protections against bounce tracking and the broader category of “navigation based tracking”.
Brave’s bounce tracking protection is just another way Brave protects your privacy online. To give a few examples, Brave prevents traditional trackers by blocking third-party cookies, using a system we call site-length, ephemeral third party storage. Brave prevents trackers from using browser fingerprinting to identify (and re-identify) you by randomizing your browser fingerprint, and Brave further prevents sites from tracking you by blocking (and sometimes replacing) known tracking scripts.






