Brave warns US Senate & Congress: foreign state actors can use targeted ads to run code on US government computers, exploiting conventional browsers
Latest updates: read more about the RTB complaints.
Brave has written to the US Senate and Congress Homeland Security Committees about a serious national security vulnerability.
In a letter sent to the US Senate and Congress Homeland Security Committees today, Brave warns that conventional web browsers allow foreign state actors to execute code on US government computers by using targeted online ads.
US federal agency and employee computers and devices are vulnerable to cyberattack by foreign state actors and criminals using “malvertising”. As the US National Security Agency has reported, “advertising has been a known malware distribution vector for over a decade”.
Brave provides the Committees with a comparative table of the security protections of web browsers, and urges them to ensure that every federal employee is provided with a web browser that blocks malvertising by default.
Today, Brave launches the next-generation Brave 1.0 on all platforms.
Download table of browser protections (PDF)
The Hon. Ron Johnson, Chairman, Homeland Security and Homeland Security and Governmental Affairs Committee
The Hon. Gary Peters. Ranking Member, Homeland Security and Homeland Security and Governmental Affairs Committee
The Hon. Bennie G. Thompson, Chairman, House Homeland Security Committee
The Hon. Mike Rogers, Ranking Member, House Homeland Security Committee
13 November 2019
Re: “Malvertising” cybersecurity threat to US federal agency and employee devices.
Dear Senator Johnson, Senator Peters, Congressman Thompson, and Congressman Rogers,
I represent Brave, a rapidly growing Internet browser based in San Francisco. Brave’s CEO, Brendan Eich, is the inventor of JavaScript, and co-founded Mozilla/Firefox. Brave is headquartered in San Francisco. I write to urge action to protect federal agency and employee computers and devices from cyberattacks by foreign state actors and criminals through “malvertising”.
This issue has been the subject of public guidance from the National Security Agency, which I attach for your convenience.
The NSA warned in June 2018 that foreign state actors can execute software on US government computers by buying targeted ads and including malicious code in the body of the ad being delivered. Government computers and devices are vulnerable to these malvertising attacks because the web browsers used by government agencies do not automatically block such ads.
The NSA warns that “web browsers present a major cyber security risk” and that “‘malvertising’ allows a malicious actor to target users based on location, interests, browsing habits, and system specific identifiers…”.
In 2017, Senator Wyden requested that the Department of Homeland Security issue a binding operational directive to require that all agencies block internet ads containing executable code. Senator Wyden renewed this call again in December 2018. These letters are also attached herewith for your convenience.
Two years have passed since Senator Wyden highlighted the acute threat posed by malvertising. Indeed, as the NSA notes, “advertising has been a known malware distribution vector for over a decade”. Despite this, computers and devices at federal agencies remain vulnerable. It should not be possible for a foreign spy to pull out a credit card and buy the ability to run executable software code on US Government devices.
Individual employees appear to have to decide for themselves whether to take measures to protect their organizations from malvertising cyberattack. The table below shows the diverse range of protection provided by web browsers.
Given the serious national security threat posed by advertisements, and the advertising industry’s failure to meaningfully address this threat, we urge your Committees to direct the Department of Homeland Security and the National Institute of Standards and Technology to review the vulnerability of web browsers to malvertising, and guide federal agencies on what browsers expose them to risk.
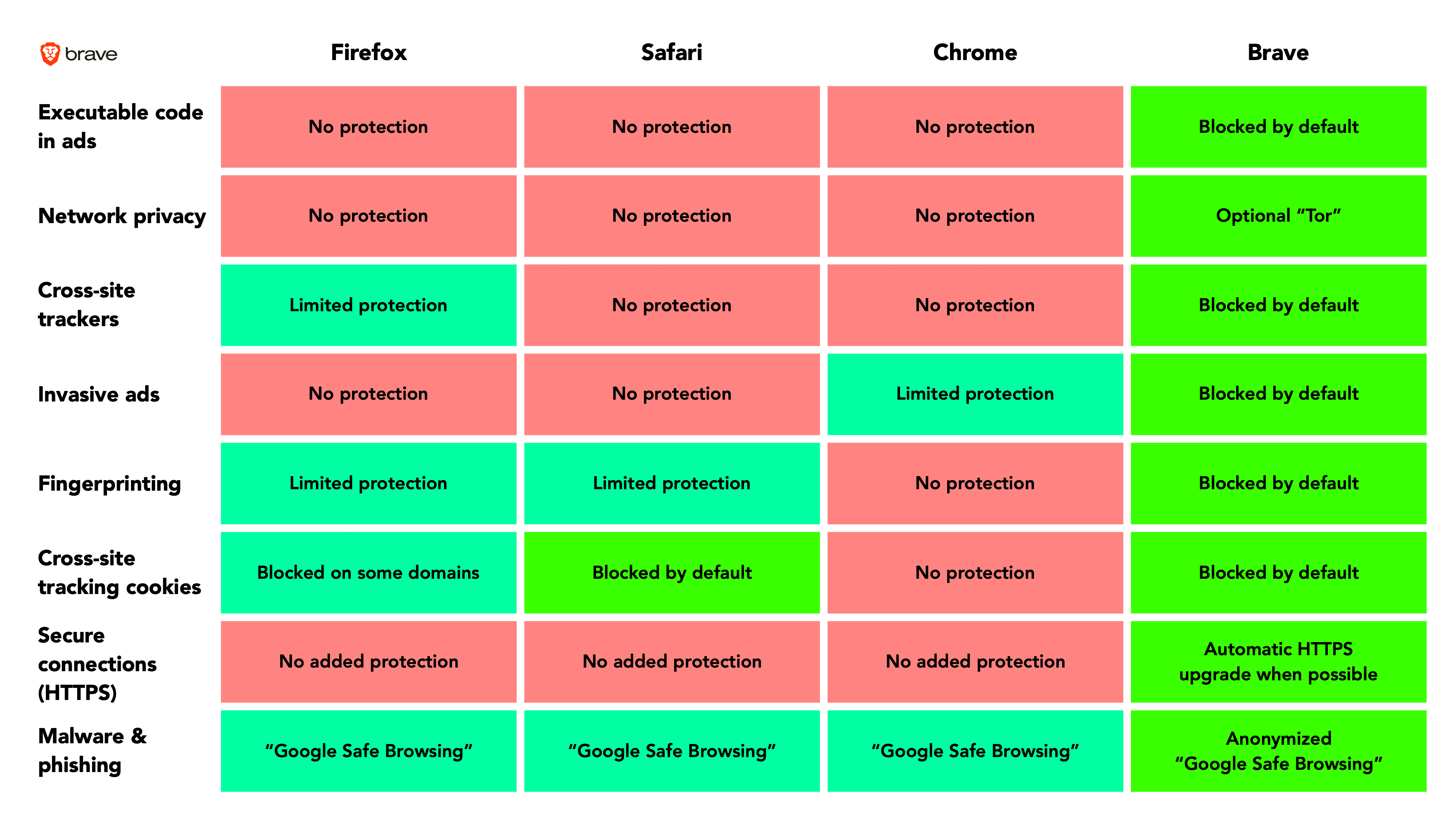
In 2018 the NSA recommended that all federal agencies “address malvertising by blocking potentially malicious, internet-based advertisements”. Every federal employee should be provided with a web browser that blocks the malvertising threat by default. It is now time to make this mandatory.
Allow me to take this opportunity to draw to your attention that Brave 1.0 launches on all platforms today.
Sincerely,

Dr Johnny Ryan
Chief Policy & Industry Relations Officer
Brave Software Inc.
CC:
Senator Ron Wyden.
General Paul M. Nakasone, Director,US National Security Agency.
Christopher Krebs, Director, US Cybersecurity and Infrastructure Security Agency.
Dr. Walter G. Copan, Director, US National Institute of Standards and Technology.
Attachments:
National Security Agency guidance “Blocking unnecessary advertising web content”.
Letter from Senator Wyden to Rob Joyce, White House Cybersecurity Coordinator.
Letter from Senator Wyden to Christopher Krebs, Director, US Cybersecurity and Infrastructure Security Agency, at the Department of Homeland Security.






